PhishReaper, Inc. uncovered a coordinated surge of phishing activity targeting QatarAirways — and the scale is alarming. Hundreds of lookalike domains were found live and reachable. Some delivered full phishing pages; others were already using basic cloaking to avoid immediate detection by redirecting visitors to the legitimate Qatar Airways site or even to neutral destinations like www.google.com. These evasive behaviors show exactly why reactive defenses fail: by the time conventional detection sees a live scam page, the attackers have already adapted.
What we found
-
Hundreds of malicious domains impersonating QatarAirways were active and reachable.
-
Delivery modes varied:
-
Direct delivery: pages serving the phishing content immediately.
-
Cloaked redirect-to-legit: pages that now redirect to the real QatarAirways site to avoid detection on cursory scans.
-
Silent redirect-to-neutral: pages that quietly redirect visitors to benign sites (e.g., google.com) to hide evidence during reconnaissance.
-
-
These tactics are a classic cat-and-mouse escalation: attackers register domains, stage content in stealthy ways, and only switch to overt phishing after initial detection windows have passed.
Hosting country distribution
Here is the hosting country distribution for these phishing websites:
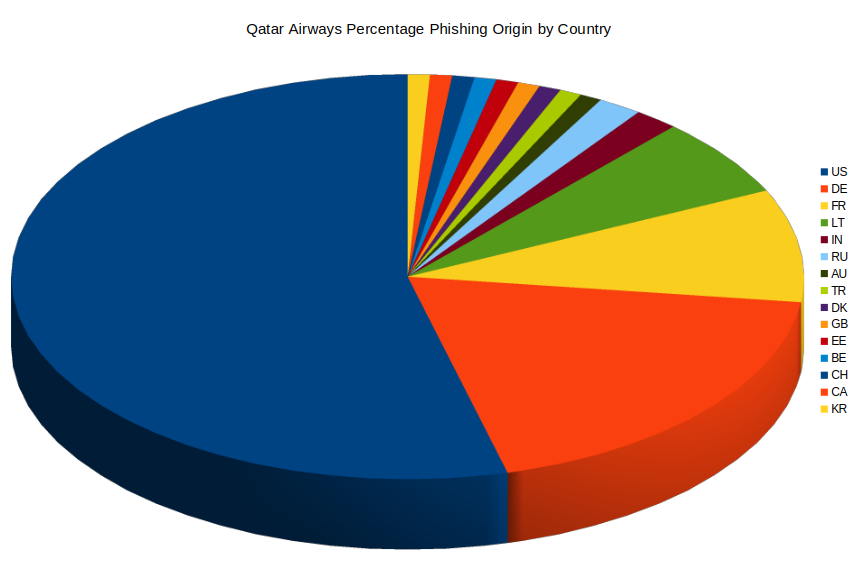
This spread shows the global footprint of inexpensive hosting and bulletproof services that attackers exploit — and why perimeter-based defenses alone can’t be relied on.
Why traditional phishing detection loses
Most defensive stacks depend on observing a malicious page or a user complaint. Attackers intentionally defeat this by:
-
Serving benign responses to quick scans or crawlers (cloaking).
-
Hosting initial assets in distributed, low-cost jurisdictions.
-
Redirecting early visitors to neutral locations to avoid creating evidence footprints.
By the time defenders see the attack surface clearly, attackers have already rotated domain content, switched infrastructure, or weaponized content for targeted campaigns on other domains.
How PhishReaper stops phishing at birth — powered by the Singularity Engine
PhishReaper’s Singularity Engine is built to end the endless cat-and-mouse chase by moving detection upstream — where phishing threats are born, not after they’ve matured. It gives defenders the first-mover advantage, spotting emerging campaigns in their infancy and stopping them long before they reach the inbox or the browser.
Instead of waiting for a phishing page to go live, the Singularity Engine continuously maps the evolving threat landscape — connecting digital signals across domain activity, hosting infrastructure, and early web patterns that indicate the shaping of a new campaign.
When a potential threat starts forming, the AI agents operating inside the engine correlate subtle signals across its global intelligence graph, evaluate the likelihood of brand impersonation, and flag malicious intent at the earliest possible moment. This proactive visibility lets security teams and partners take action before attackers can arm, cloak, or weaponize their infrastructure.
The result:
PhishReaper doesn’t just detect phishing — it prevents it from existing in the wild. By catching threats at creation, the Singularity Engine empowers organizations to stay ahead of attackers, reduce response time from days to minutes, and protect their brand before damage ever begins.
The bottom line
Attackers win time; defenders lose it. When phishing is allowed to incubate, even briefly, it becomes exponentially harder to track, remediate, and remediate again. PhishReaper flips the script by intercepting campaigns at creation, removing the attacker’s ability to quietly arm, cloak, and reuse assets.
Stop phishing before it takes flight. Detect at birth. Disrupt at scale. Defend with PhishReaper — because the best way to beat a chameleon is to catch it before it ever changes color.
(Reach out to us at support@phishreaper.ai to get the complete list of related IOCs.)


Leave a Reply