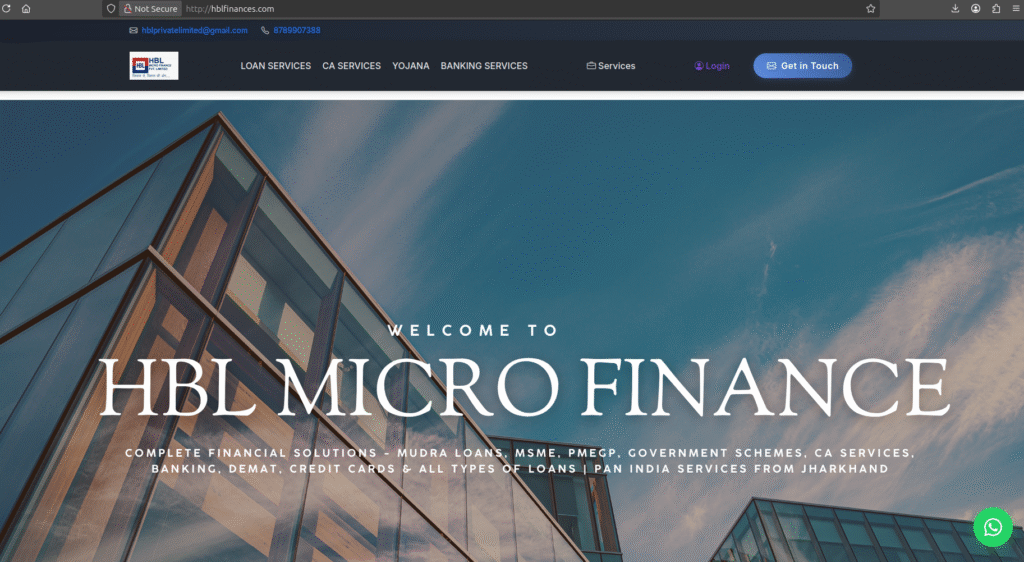
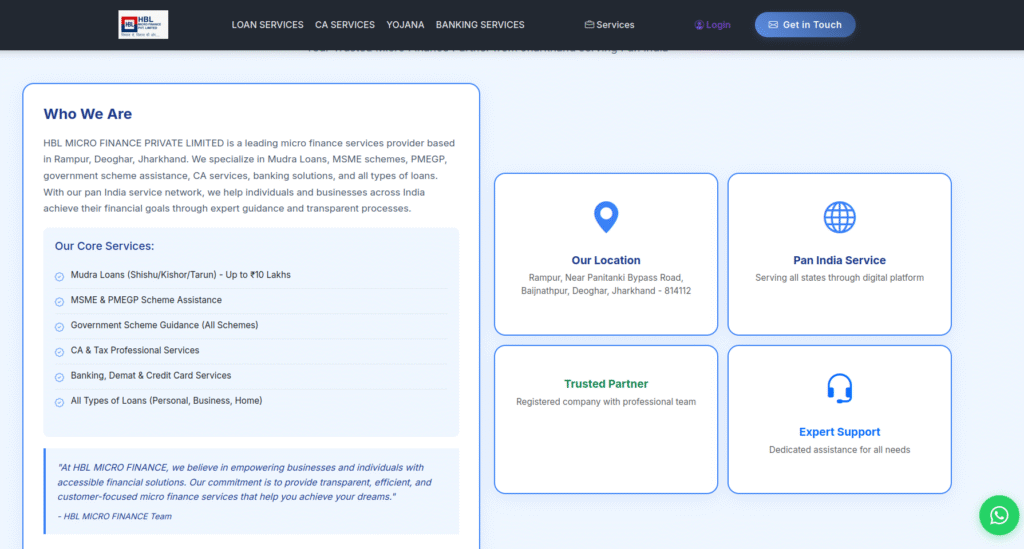
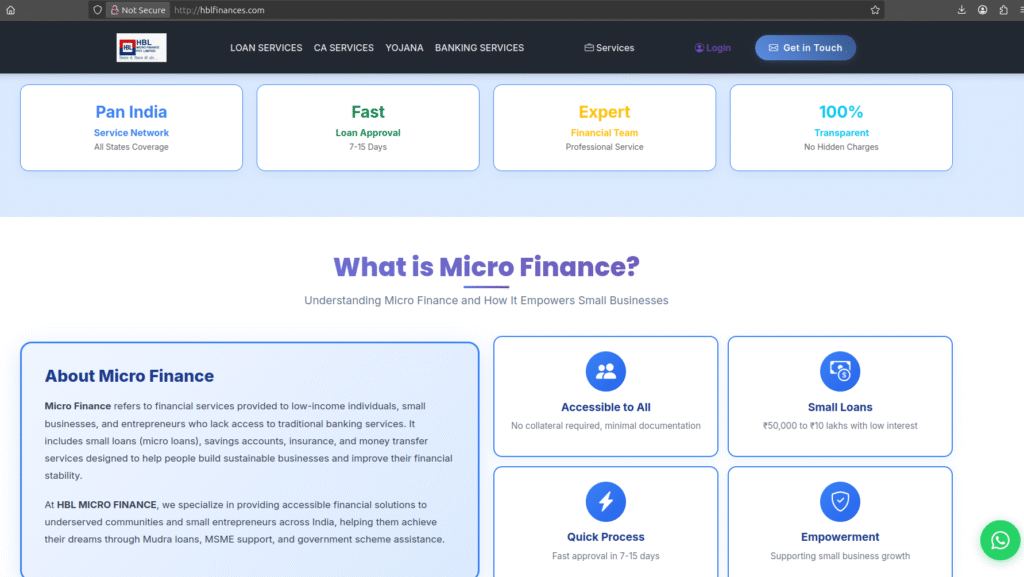
PhishReaper’s autonomous agentic AI hunter has uncovered a live, high-confidence phishing campaign, represented here by a site impersonating HBL Microfinance Bank at hblfinances[.]com. The site has been registered through GoDaddy and is being operated by a ghost entity in India. It went live on October 25, 2025 and, as of today, remains reachable and active. Visitors are funneled to an Indian WhatsApp contact via an on-site plugin and encouraged to engage with a deceptive Gmail address, hblprivatelimited@gmail.com. Alarmingly, broad reputation engines (including multi-engine aggregators) still mark the site as clean.
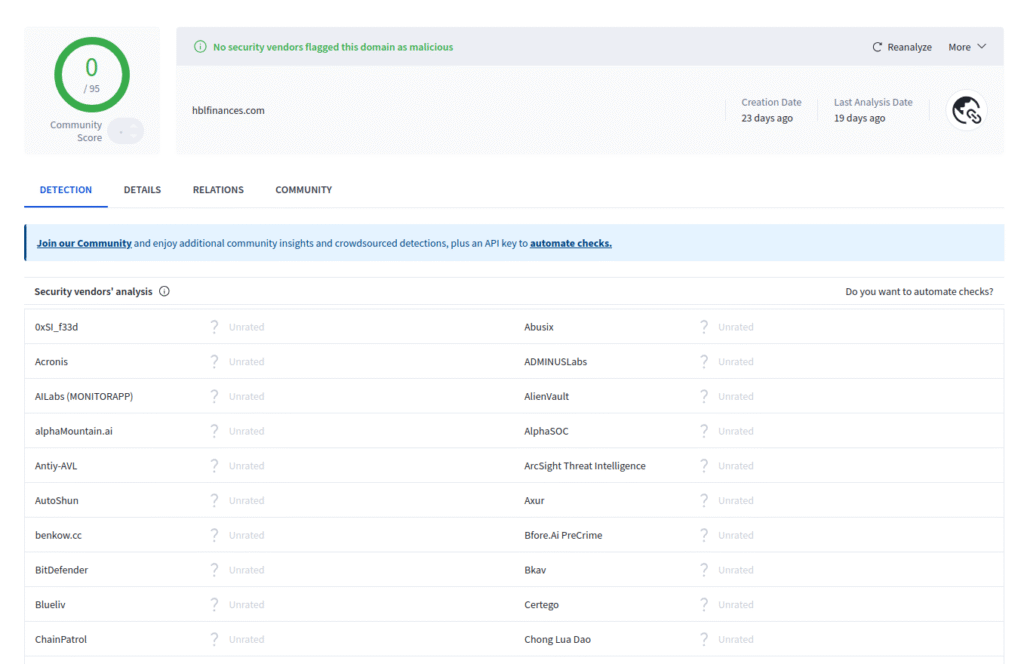
This is not a bug. It’s a feature of the current defensive posture: slow, reactive, and trusting scores over evidence. PhishReaper disagrees.
What we captured — the facts, bluntly
-
Domain:
hblfinances.com— live since 2025-10-25. -
Registrar: GoDaddy (registration visible in capture metadata).
-
Operator location (observed): India (infrastructure and traffic redirection patterns).
-
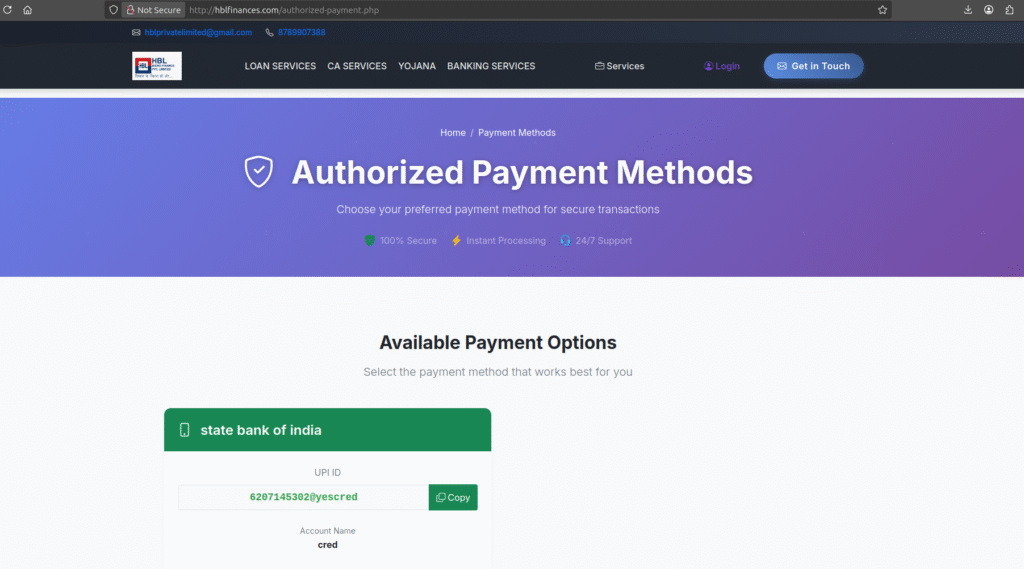
Attack vector: On-site WhatsApp plugin that routes victims to an Indian WhatsApp number; site advertises
hblprivatelimited@gmail.comto impersonate official bank contact. -
Detection gap: Multi-engine aggregators currently return no significant detections — this page has been active for 18 days without being flagged by anyone except PhishReaper.
Why this matters
High-fidelity brand impersonation + trusted messaging (WhatsApp) = fast conversion for attackers. While bulk scanners look for known indicators, attackers are weaponizing social channels and low-volume domains that fly under reputation radars. That 18-day window is an emergency: it’s long enough to harvest credentials, arrange fraudulent transfers, and erode customer trust in the brand worldwide.
Our read — what the world missed
Scanners operate on history and volume. PhishReaper operates on presence. We find look-alikes the moment they appear, capture forensic evidence, map contact vectors, and perform relentless intent similarity analysis. When everyone else returns “clean,” we return screenshots, timestamps, server headers, WHOIS/RDAP, and a mapped chain-of-contact for registrar and messaging abuse complaints.
To put it in simple words: Our Agent Reaper doesn’t sleep.
Immediate recommendations (we’re ready to act)
-
HBL Microfinance: Issue a takedown notice (we can help). Publish a customer warning naming
hblfinances.comand the WhatsApp contact used. We can provide all of the domains in this campaign. Ask customers to never authenticate via unknown Gmail addresses. -
GoDaddy / Hosting provider: Expedite abuse review — we have full-capture artifacts we will supply.
-
WhatsApp / Meta: Block the associated contact and investigate the phone number for abuse.
-
Customers: If you received messages referencing HBL and directing you to
hblfinances.comorhblprivatelimited@gmail.com, do not reply — contact your bank through official channels.
Final word
Eighteen days is an eternity in fraud terms. When brand impersonation is live for weeks and VirusTotal shows “clean”, the answer isn’t silence or hope — it’s active hunting. PhishReaper found the site on October 25, 2025. It’s still live on November 13, 2025. That gap costs money, customers, and reputation. Some might even end up losing their entire life savings. We don’t accept it.


Leave a Reply