As the holiday season is approaching worldwide, scammers are coming up with interesting new ways of credential harvesting around global payment platforms such as Mastercard among many others.
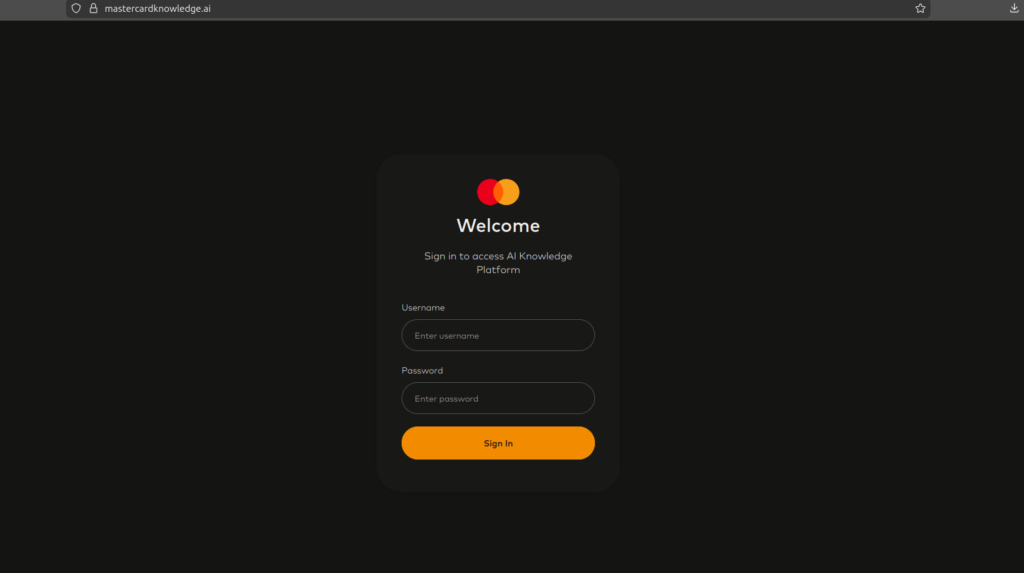 Besides several “Mastercard Casinos” and “Mastercard Prime Card” websites offering “discounts” on Google Play and Amazon, there is a new twist in the bunch. This particular one is hosted on mastercardknowledge.ai, a domain that has been in “maturing stage” since August, 2025. The HTML itself contains enough signals to classify this as high-confidence credential-harvesting phishing, without needing network traffic or backend access.
Besides several “Mastercard Casinos” and “Mastercard Prime Card” websites offering “discounts” on Google Play and Amazon, there is a new twist in the bunch. This particular one is hosted on mastercardknowledge.ai, a domain that has been in “maturing stage” since August, 2025. The HTML itself contains enough signals to classify this as high-confidence credential-harvesting phishing, without needing network traffic or backend access.
1: WordPress authentication artifact in Plain Sight
<input type=”hidden” name=”remember” value=”1″ />
<!– remember=1 makes the WP auth cookie long-lived –>
This explicitly references WordPress authentication behavior. Mastercard does not use WordPress-based auth for enterprise platforms. This line alone strongly suggests a repurposed phishing kit or a custom WordPress credential handler.
2: Raw Credential Harvesting Form (No Enterprise Auth)
<form id=”loginForm” autocomplete=”on”>
<input name=”username” type=”text” autocomplete=”username”>
<input name=”password” type=”password” autocomplete=”current-password”>
</form>
There is:
-
no SSO redirect,
-
no OAuth/OpenID flow,
-
no device trust bootstrap,
-
no MFA step.
Mastercard authentication relies on federated identity and step-up verification, not direct password submission in static HTML.
This is textbook credential capture.
3. Intentional Discovery Suppression
<meta name=”robots” content=”noindex, nofollow”>
This is a common phishing tactic to:
-
evade search indexing,
-
reduce exposure to automated brand monitoring,
-
delay takedown detection.
Legitimate Mastercard login portals are discoverable and documented, even if access is restricted.
4: Asset & Hosting Inconsistencies
<link rel=”stylesheet” href=”/assets/css/app.css”>
<script src=”/assets/js/app.js”></script>
All assets are:
-
locally hosted,
-
generically named,
-
detached from Mastercard’s known CDN patterns (Akamai, branded asset domains).
This strongly suggests a standalone deployment, not a Mastercard-managed environment.
5: Absence of Mandatory Enterprise Signals
The page contains none of the following, all of which are standard for Mastercard properties:
-
legal footer or copyright notice,
-
privacy or data-handling policy,
-
regulatory or compliance disclosures,
-
tenant or organization context.
For a payments network, this absence is not an oversight. It’s a red flag!
6: Brand Lure + Vague Platform Naming
The title and copy:
<title>AI Knowledge Platform</title>
<p>Sign in to access AI Knowledge Platform</p>
This naming is intentionally generic:
-
no product documentation,
-
no user context,
-
no explanation of purpose.
This lowers user skepticism and accelerates credential submission which is a known phishing optimization.
Conclusion: Why This Page Never Should Have Existed
This page is not sophisticated. It is early, quiet, and dangerous.
Everything about it; from the WordPress auth artifact to the raw credential form and deliberate discovery suppression; points to a phishing operation designed to exist just long enough to steal access and disappear.
Most security stacks will eventually catch this after credentials are widely abused. Most feeds will eventually see it after a large scale damage is done.
PhishReaper exists to catch it before that. Our platform detected this phishing website back in August on the same day when it was quietly created with nothing hosted on it yet. And here we are, 4 months later, and the website is now alive and stealing.
It should have been taken down before the login page was able to claim its first victim; before a brand’s name became a weapon. However, 4 months later, the detection world is still oblivious of what this website, and millions of others like this, are doing out there in the wild; awaiting victims.
Fraud does not deserve reaction time. It deserves removal at inception.
This page is exactly the kind of deception PhishReaper was built to erase; not by waiting for compromise, but by ensuring it never gets the chance to happen. Here are a few others out of millions that are still conveniently flying under the detection world’s radar.



Leave a Reply