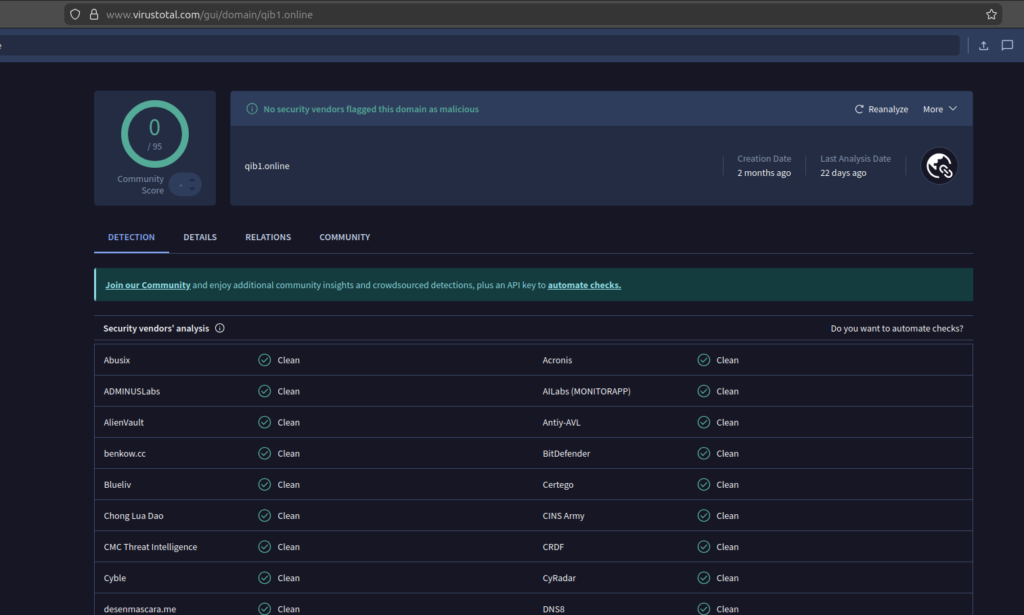
A Qatar Islamic Bank (QIB) impersonation domain (qib1[.]online) was registered on 4 October 2025 and detected by PhishReaper’s agentic AI on the same day. However, it was still active as of 25 December 2025; i.e., An 82‑day operating window. In phishing, time is not a detail. Time is the multiplier.
Why 82 Days Matter
An 82‑day lifespan is not a “single incident.” It is a sustained harvesting operation. It provides enough time for redistribution across multiple waves (SMS, WhatsApp, email forwards), enough time for victims to cycle, and enough time for fraud to surface long after data is captured. If detection starts at chargebacks, the defender is measuring the end of the story; not stopping the beginning.
Source Code Dissection (What the Page Was Built to Do)
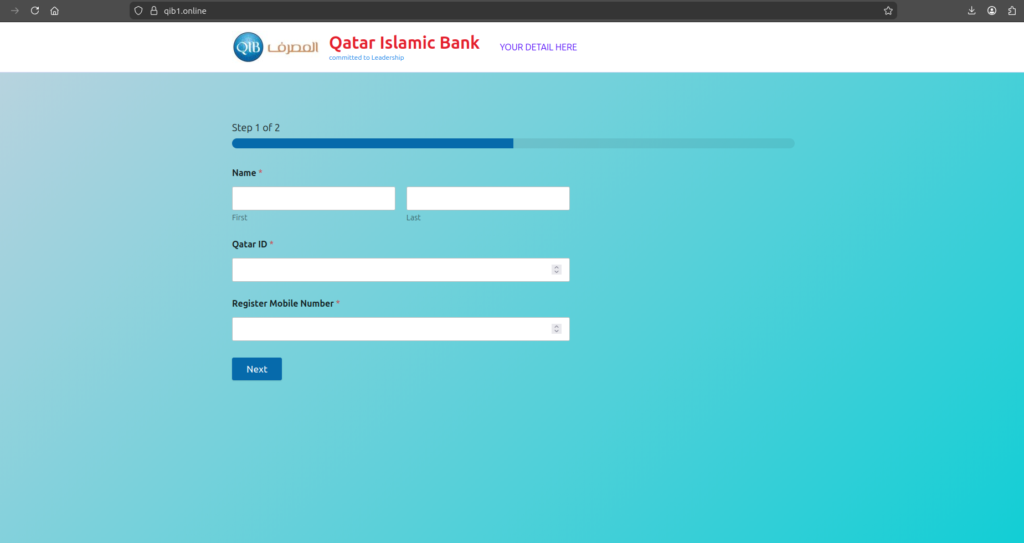
This page is engineered for “structured data theft”, not “generic login phishing”.
Harvested fields observed in the source:
• Identity anchors: customer name, Qatar ID (national identifier), registered mobile number.
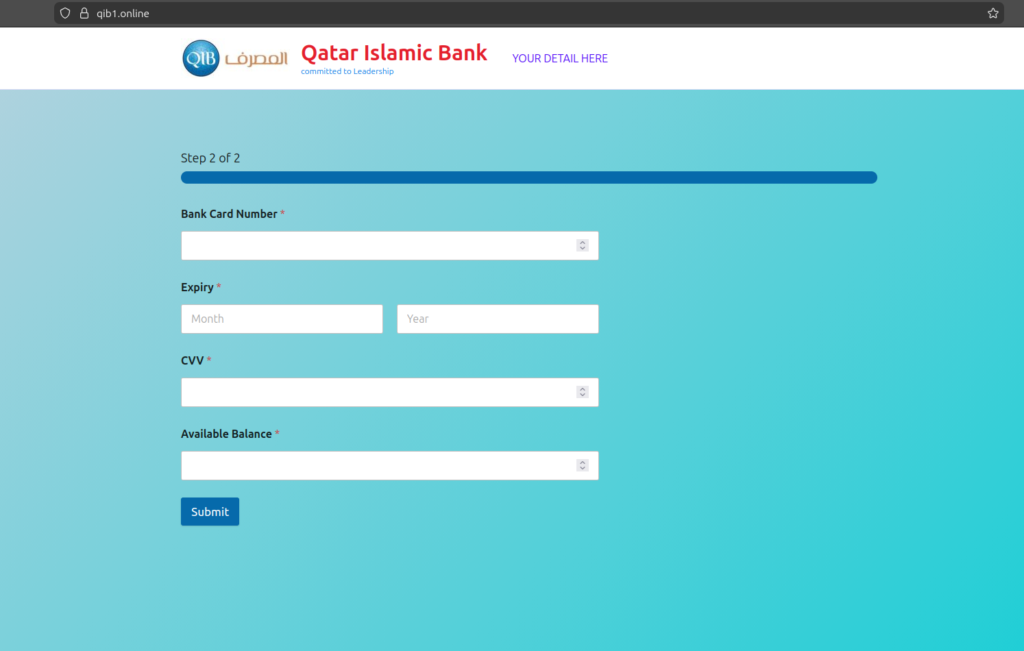
• Payment credentials: card number (PAN), expiry month/year, CVV.
• Victim triage: available balance (used to prioritize high‑value victims).
Observed flow:
• Two-step workflow: identity + contact first, then full card capture.
• This sequencing increases completion rates: victims “commit” with low-friction fields before entering high-risk data.
Operational implementation details that matter to defenders:
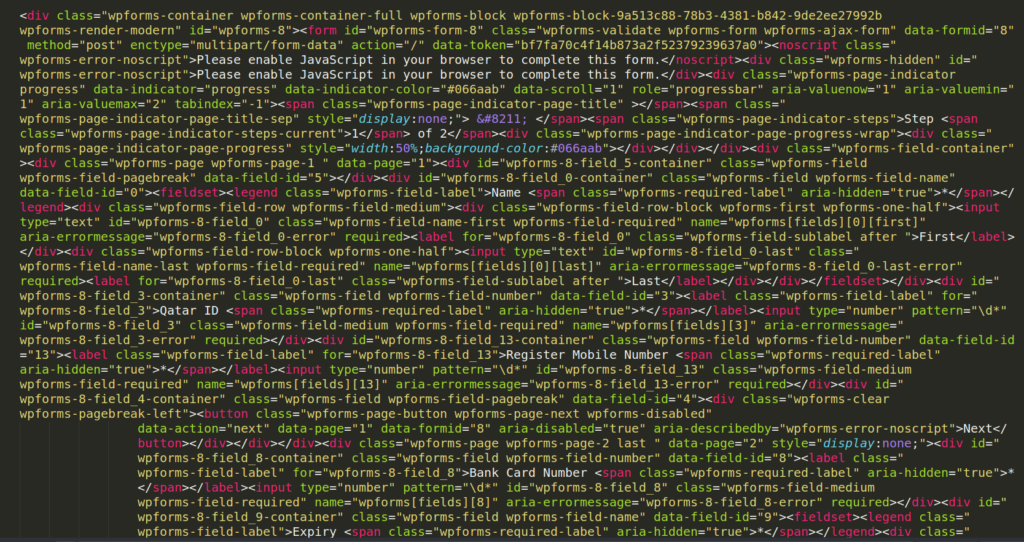
• Built on WordPress with a common forms stack (WPForms).
• Form submission routed through WordPress AJAX handler: /wp-admin/admin-ajax.php on the phishing domain.
• WPForms commonly stores submissions server-side and/or emails them (attacker-controlled configuration), meaning exfiltration can look like “normal CMS behavior” rather than custom malware JavaScript.
Observed Indicators & Artifacts (from Source)
• Domain: qib1[.]online
• Submission endpoint: https://qib1.online/wp-admin/admin-ajax.php
• WPForms markers: wpforms-ajax-form present; data-formid=”8″ referenced in the HTML/JS configuration.
• Branding cues: QIB naming and leadership tagline used to increase trust and reduce suspicion.
Risk If QIB Waits (What Happens in Practice)
If QIB relies on reactive signals (complaints, fraud disputes, chargebacks), the attacker keeps the advantage. With full card credentials (PAN/EXP/CVV) captured, monetization does not require additional compromise. The inclusion of a registered mobile number and national ID elevates risk beyond card fraud into OTP targeting, SIM‑swap attempts, and follow‑on impersonation.
What increases with every day the domain remains active:
• Victim count (more distribution cycles).
• Loss per victim (attackers focus on high-balance submissions).
• Operational burden (fraud ops, call center load, reputational damage).
• Compliance exposure (incident handling, customer remediation, reporting obligations depending on policy/jurisdiction).
Why PhishReaper Exists (Collapse the Window)
PhishReaper is not designed to “block a URL after victims report it.” It is designed to reduce the time‑to‑awareness from weeks/months to hours by surfacing brand‑impersonating domains early, scoring intent, and triggering takedown/blocking/customer-warning actions before campaigns scale.
A phishing site killed on day one is an inconvenience. A phishing site alive for 82 days becomes a business.
The Bottom Line
This incident did not rely on zero‑days or advanced tooling. It relied on time.
Fraud does not announce itself. It does not wait for quarterly reviews. It does not pause for internal escalation paths. It exploits time.
An 82-day phishing operation is not a technical anomaly. It is a predictable outcome when detection begins after victims report loss. PhishReaper exists to break this pattern; to surface malicious intent at inception, to collapse attacker dwell time from months to hours, and to ensure that brand trust is defended before it is monetized by criminals.
In phishing, the question is never if damage occurs. It is how long defenders allow attackers to operate before intervening.


Leave a Reply