PhishReaper’s Agentic Singularity pool sent some suspicious intelligence signals around the Stripe brand to our AI agents browsing different parts of the web 2 weeks ago — subtle enough for legacy systems to ignore, loud enough for us to listen. That trail led straight to a big phishing campaign targeting Stripe, the internationally used and widely deployed payment gateway. Let’s take StripePay.online, a domain out of several dozen involved in that campaign, as a case study, which was created on 13 November 2025.
Today marks 2 full weeks since its creation. Not only did it stay unarmed for a good week as our agents tracked it, as of today it’s been armed for several days and is being actively used to steal credit cards worldwide.
Two weeks old. Live. Freely harvesting credit and debit cards from worldwide victims.
Two weeks of global visibility.
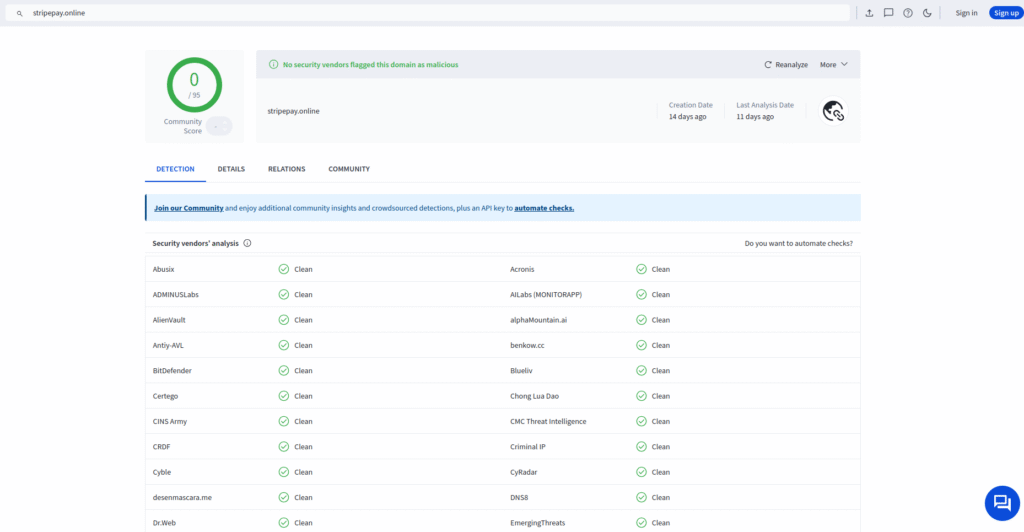
Two weeks of zero detections from the entire detection world.
PhishReaper: Detected on first encounter 2 weeks ago along with the entire campaign family.
What the world missed
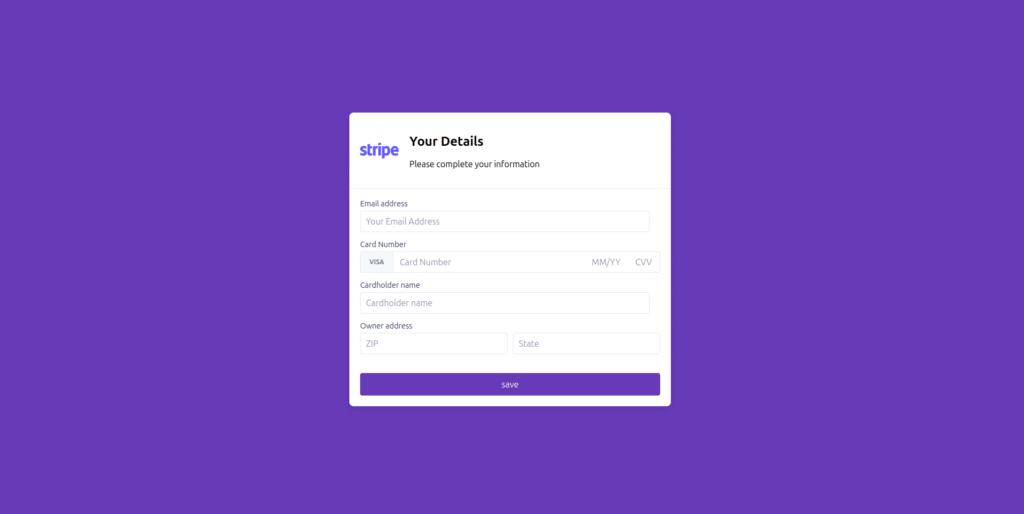
StripePay.online impersonates Stripe’s verification flow with cloned UI, clean typography, and a reassuring purple theme. But beneath the surface, the anomalies are textbook phishing:
-
No Stripe.js — the one component Stripe never operates without
-
Raw PCI fields in HTML — card number, expiry, CVV, ZIP, name
-
Wikipedia-hosted logo — classic evasion pattern used in fast-rotating kits
-
save.phpbackend — a skimmer endpoint dressed as a payment processor -
Fake loading delay — masking immediate exfiltration
-
Temporal clustering with other Stripe lookalike infrastructure
These signals don’t appear in threat feeds, hashes, or blocklists — because the campaign hasn’t been reported, crawled, or abused loudly enough for legacy tools to notice, yet!
And that’s the problem.
The entire phishing detection cybersecurity industry collectively reacts to history.
Meanwhile, PhishReaper hunts the hunters.
Why PhishReaper found it immediately
Our autonomous agents track threat actor activities, behavioral drift, intent anomalies, brand impersonation vectors, UI anomalies, and infrastructure overlap among dozens of other bleeding-edge algorithms — the precursors of phishing activity, not the aftermath.
StripePay.online was never “clean”.
It was simply “undetected” by every other system.
Two weeks of silence from the world.
One pass from PhishReaper — and the deception collapsed.
A Word to CISOs and SOC Teams
If your defenses depend on traditional feeds, blocklists, DNS reputation, or enrichment-based classical engines, you are already behind. StripePay.online and the rest of the campaign proves the gap: a live, high-fidelity phishing campaign running unopposed for 14 days because the world’s most trusted detection stacks never saw it.
This is your wake-up call.
Phishing has evolved.
Your adversaries have evolved.
Your detection stack must evolve too.
Integrate PhishReaper.
Not as just another feed — but as your forward-facing early-warning layer.
We catch what the world never manages to report, although it silently harms millions and causes breaches & security incidents worldwide.
To the architects of this campaign and other phishing campaigns: You can hide from the world. You cannot hide from PhishReaper. And once you’re seen, there is no returning to the dark.


Leave a Reply