How a Live Google-Impersonation Network is born and now operating in Plain Sight — Undetected
Executive Summary
Over the past couple of days, PhishReaper identified multiple Google-impersonating domains that are churning out into the wild courtesy some professional threat actors with very specific industry targeting habits — some redirecting to legitimate Google properties, others serving staged infrastructure, and many others are delivering malicious Chrome look-alike payloads that remain undetected on VirusTotal.
None of these domains were flagged by mainstream blocklists, commercial threat feeds or popular web browsers.
This is not a failure of a single vendor.
This is a systemic failure of how the world still thinks phishing works.
The Illusion of Safety: “It Redirects to Google, So It Must Be Fine”
Several domains in this cluster were deliberately engineered to appear benign:
-
protected-google[.]com(created on 13 Jan, 2026) → redirects togoogle.com -
helps-google[.]com(created on 13 Jan, 2026) → redirects togoogle.com -
accountrecover-google[.]com(created on 15 Jan, 2026) → redirects togoogle.com
This is not accidental.
This is reputation laundering.
Why this works
Most automated scanners:
-
Fetch the homepage
-
Observe a clean redirect
-
Mark the domain as “benign”
No one asks:
-
What happens on a specific path?
-
What happens after a time delay?
-
What happens based on User-Agent, geo, or referrer?
PhishReaper’s Agentic AI does.
Dormant Infrastructure: The “Dead” Domains That Aren’t Dead
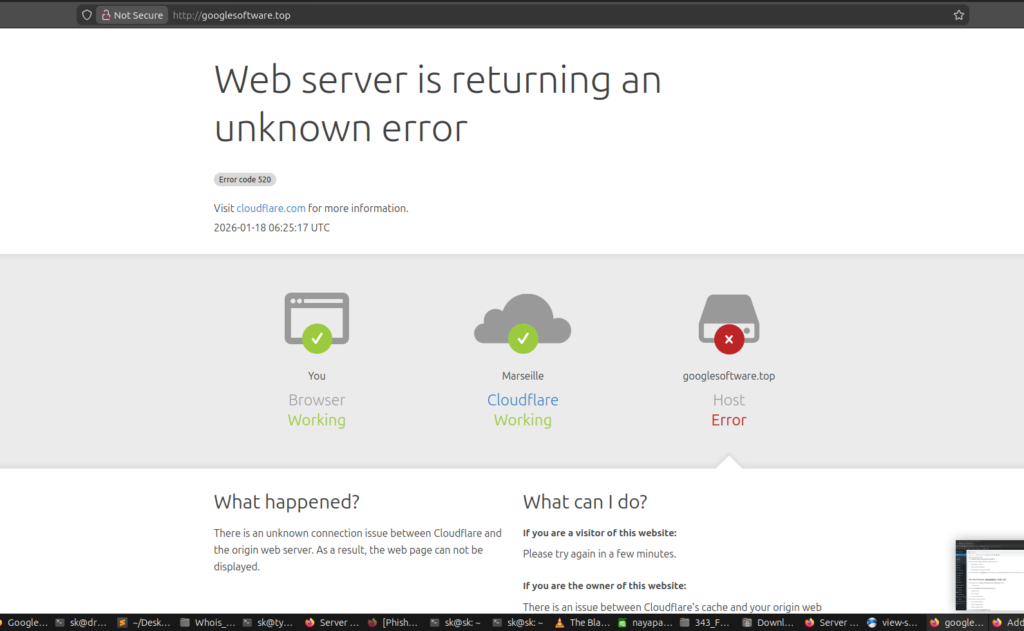
googlesoftware[.]top
Returns a Cloudflare host error.
To most systems, this looks like:
“Inactive. Ignore.”
To an adversary, this means:
-
DNS is live
-
TLS is valid
-
Reputation is aging
-
Payload can be armed later in minutes
This is pre-positioned phishing infrastructure, not a dead site.
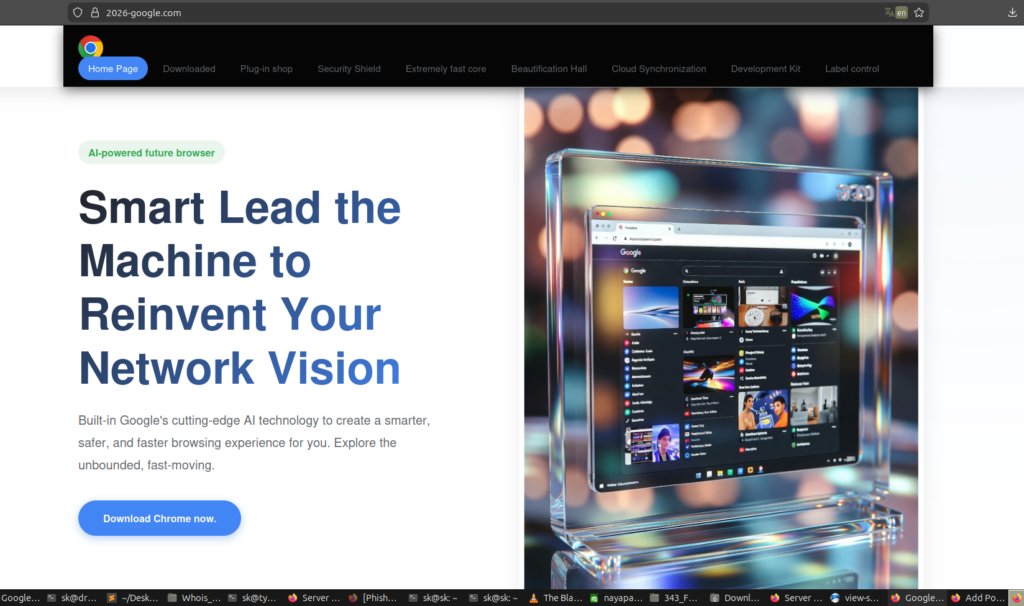
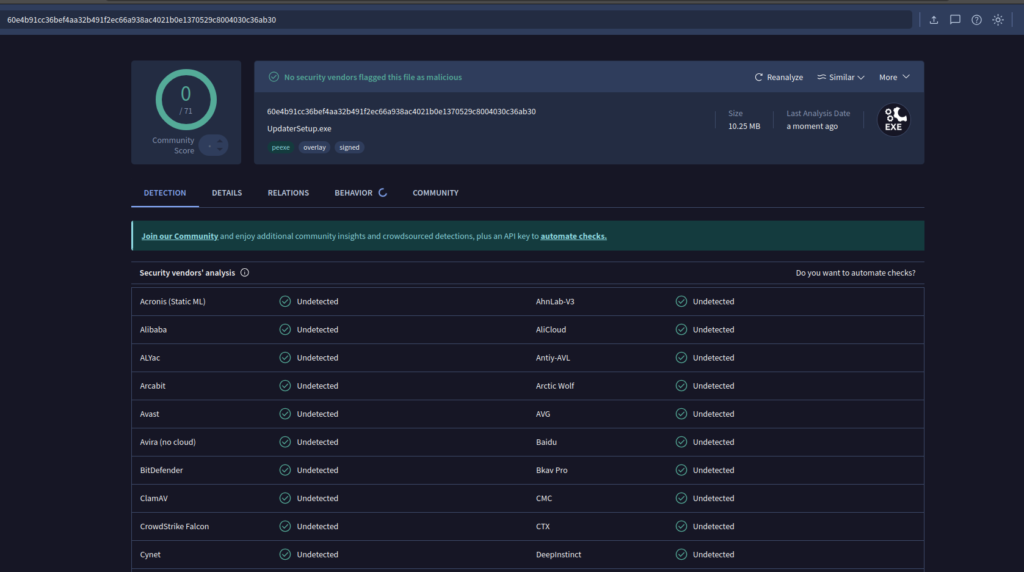
A Fake Chrome Download That Nobody Detected
2026-google[.]com
This domain serves what appears to be a Google Chrome download page. But:
-
The binary is not legitimate
-
VirusTotal detection: 0 / 71
-
Hosting and delivery chain are clean
-
No signature-based engine triggered
This is the perfect nightmare scenario:
-
Brand-perfect lure
-
Trusted software theme
-
Undetected payload
-
Zero public intelligence coverage
This is post-signature phishing.
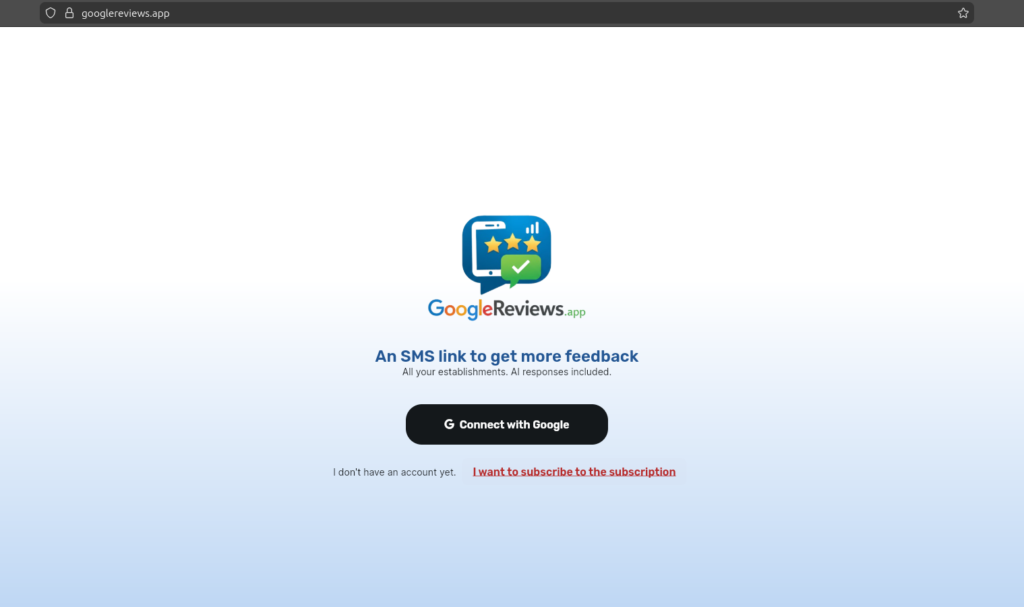
FlutterFlow Phishing-as-a-Service: googlereviews[.]app
At first glance, the source code looks harmless.
It’s a Flutter web application, hosted via Google Cloud Storage, built with FlutterFlow.
Key observations:
-
meta name="robots" content="noindex"
→ Explicit intent to avoid search engine discovery -
Assets hosted on:
-
Legitimate Google infrastructure used to host a Google-branded phishing surface
This is not amateur phishing.
This is platform abuse with plausible deniability.
Security tools still struggle to label this as malicious because:
-
The hosting is “trusted”
-
The framework is legitimate
-
The page itself is dynamically rendered
Most tools hesitate here. PhishReaper does not hesitate. A Google-branded application deployed outside Google’s control is not “interesting.” It is hostile.
The Ghost Domain: wkd-google[.]com[.]cn
This domain returns a Chinese hosting provider default page stating:
“No site found”
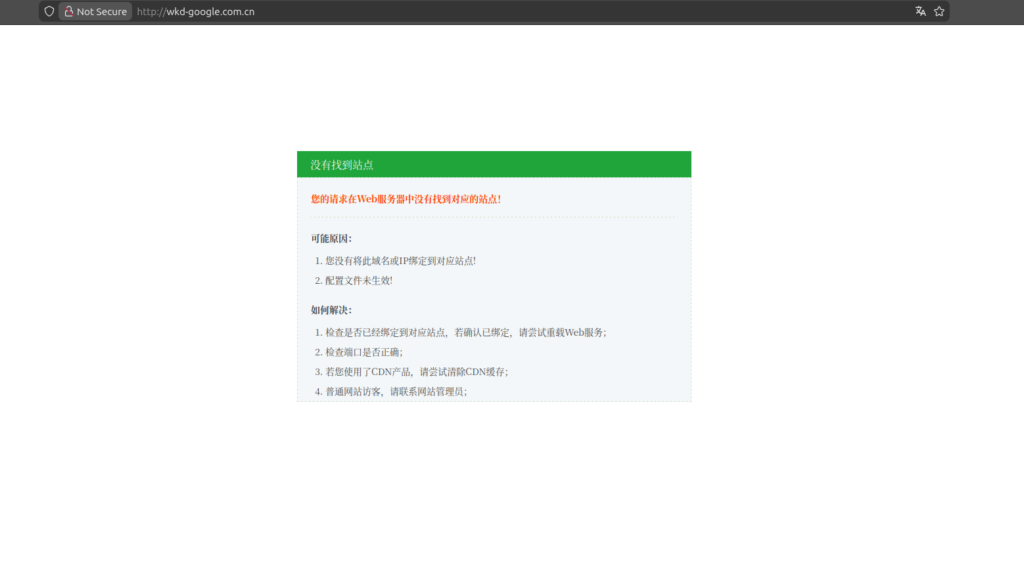 This is classic unbound virtual host infrastructure:
This is classic unbound virtual host infrastructure:
-
Domain resolves
-
Server responds
-
No active site bound yet
These domains are often activated:
-
Hours before campaigns
-
Only for specific regions
-
Only for specific victims
They exist to evade pre-arming detection.
The Bigger Failure: Why Nobody Saw This
Let’s be blunt.
The global phishing defense ecosystem still relies on blocklists, static reputation, file hash scanning and naive redirects checks.
Attackers have moved on a long time ago.
What they are doing now:
-
Staging domains months in advance
-
Redirect laundering
-
Conditional payload delivery
-
Abuse of trusted cloud platforms
-
Framework-based phishing apps
-
Zero-day malware delivery through brand trust
And yet:
-
These domains are not in feeds
-
Not in browsers
-
Not in mail gateways
-
Not in endpoint tools
They exist outside the worldview of legacy detection.
Why PhishReaper’s Agentic AI Detected Them
PhishReaper does not ask:
“Is this domain already known to be bad?”
PhishReaper asks:
“Why does this domain exist at all?”
Our Agentic AI analyzes:
-
Brand-token abuse at scale
-
Domain intent, not reputation
-
Infrastructure staging patterns
-
Framework misuse
-
Hosting semantics
-
Redirect deception
-
Behavioral fingerprints
- History of the creators
This is Agentic AI doing threat hunting, not threat lookup.
Final Thought
What makes this detection meaningful is not that PhishReaper eventually caught these domains. It’s that PhishReaper caught them without waiting. No user reports. No phishing emails observed. No malware callbacks. No consensus feeds.
These domains were detected because PhishReaper understands something the rest of the industry still struggles with: phishing infrastructure no longer reveals itself through damage. It reveals itself through purpose, or what we call INTENT.
Being first matters. Not first to respond — first to see. While others wait for proof, PhishReaper acts on intent. That is why brand-new Google impersonation domains don’t get a grace period. They get flagged. These domains were new. They were live. They were already doing what phishing infrastructure is designed to do.
PhishReaper was already there.
That is not incremental improvement.
That is a different league of detection.
These Google-impersonation domains were not hidden. They were not sophisticated exploits. They were not zero-day vulnerabilities.
They were simply ignored. Ignored because the industry is still playing defense with yesterday’s assumptions.


Leave a Reply